Frosty Keypad
Objective
In a swirl of shredded paper, lies the key. Can you unlock the shredder’s code and uncover Santa’s lost secrets?
Hints
UV light
Numbers found from lighting at the keypad using the UV light:
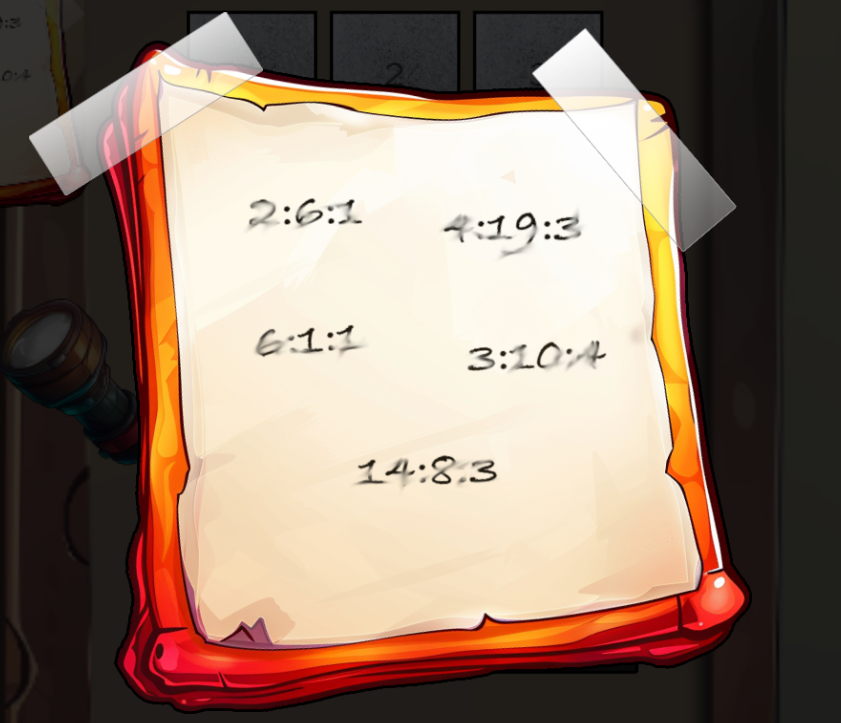
[ 2, 6, 7, 8 ]Hint from the book
This is the hint we get:
Thinking about it, it appears to correpond to
page:word:letterUsing this formula I got:
| Sequence | From book |
|---|---|
| 2:6:1 | S |
| 4:19:3 | A |
| 6:1:1 | N |
| 3:10:4 | T |
| 14:8:3 | A |
Somehow I got “SANTA”. After much thoughtwork I came up with a scheme on how I can use this word - let’s look at it with some Regex filter spectacles:
| Position | Letter | Pattern |
|---|---|---|
| 1 | S | Pos 1 should not be same as pos. 5 |
| 2 | A | Pos 2 should be the same as pos. 5 |
| 3 | N | Pos 3 should not be the same as pos, 1, 2, 4, 5 |
| 4 | T | Pos 4 should not be the same as post 1, 2, 3, 5 |
| 5 | A | Pos 5 should be the same as pos. 2 |
Solution
Silver
Bruteforcer
Given the filter outlined under “Hint from the book”, I created the following Python script to calcualte permutations and apply the filter scheme. I picked up the the remote URL and POST format from a BurpSuite session. The script:
import requests, itertools, time
for perm in [''.join(p) for p in itertools.product(['2', '6', '7', '8'], repeat=5)]:
if perm[0] is not perm[-1] and perm[1] == perm[-1]:
if (perm[0] not in list(set(perm[2:4]))) and (perm[1] not in list(set(perm[2:4]))) and len(list(set(perm[2:4]))) > 1:
res = requests.post(
"https://hhc24-frostykeypad.holidayhackchallenge.com/submit",
json = { "answer": perm }
)
if res.status_code != 400:
print(perm)
break
else:
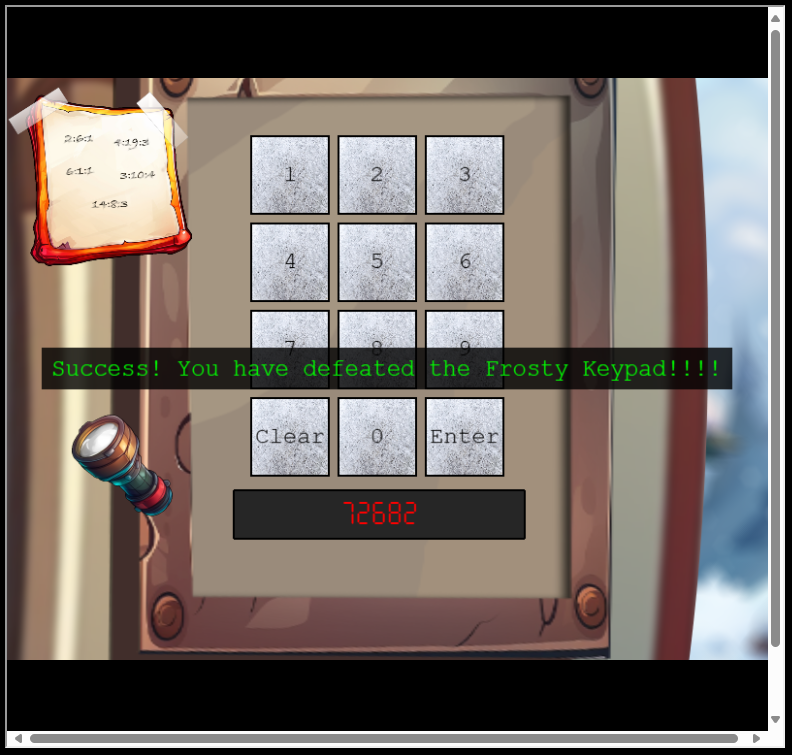
time.sleep(1)After just a couple of seconds, it produced the correct pin code:
72682As evident here, the pincode got accepted:
Gold
There’s a second pincode to be found that doesn’t fit the tips already given. Time to modify the above script and bruteforce the solution:
import requests, itertools, time
for perm in [''.join(p) for p in itertools.product(['2', '6', '7', '8'], repeat=5)]:
print(f"trying '{perm}' ... ", end="")
res = requests.post(
"https://hhc24-frostykeypad.holidayhackchallenge.com/submit",
json = { "answer": perm }
)
if res.status_code != 400:
print(f"{res.status_code} - {res.json()} - {perm}")
else:
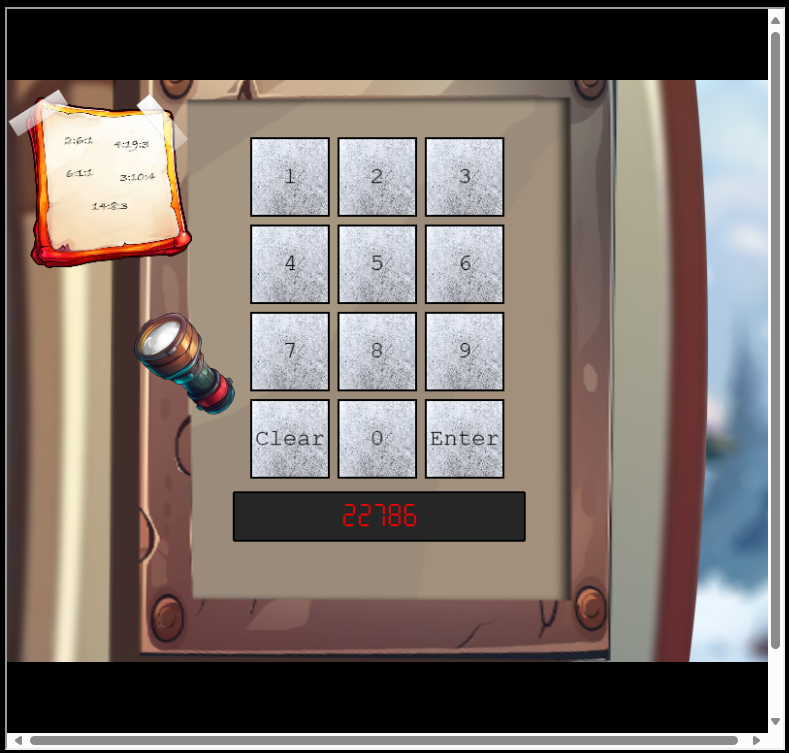
print(" Negative")
time.sleep(1)This script found the other pincode within seconds: 22786